Apple Platform Security
- Intro to Apple platform security
- Hardware security overview
- Apple SoC security
- Secure Enclave
- Face ID and Touch ID security
- Magic Keyboard with Touch ID
- Face ID, Touch ID, passcodes, and passwords
- Facial matching security
- Uses for Face ID and Touch ID
- Secure intent and connections to the Secure Enclave
- Hardware microphone disconnect
- Express Cards with power reserve
- System security overview
- Boot process for iOS and iPadOS devices
- Memory safe iBoot implementation
- Boot process
- Paired recoveryOS restrictions
- Startup Disk security policy control
- LocalPolicy signing-key creation and management
- Contents of a LocalPolicy file for a Mac with Apple silicon
- Startup Security Utility
- Firmware password protection
- recoveryOS and diagnostics environments
- Signed system volume security
- Secure software updates
- Operating system integrity
- Additional macOS system security capabilities
- System Integrity Protection
- Trust caches
- Peripheral processor security
- Rosetta 2 on a Mac with Apple silicon
- Direct memory access protections
- Kernel extensions
- Option ROM security
- UEFI firmware security in an Intel-based Mac
- System security for watchOS
- Random number generation
- Apple Security Research Device
- Encryption and Data Protection overview
- Passcodes and passwords
- Data Protection overview
- Data Protection
- Data Protection classes
- Keybags for Data Protection
- Protecting keys in alternate boot modes
- Protecting user data in the face of attack
- Sealed Key Protection (SKP)
- Activating data connections securely in iOS and iPadOS
- Role of Apple File System
- Keychain data protection
- Volume encryption with FileVault
- Managing FileVault
- Protecting app access to user data
- Protecting access to user’s health data
- Digital signing and encryption
- App security overview
- Intro to app security for iOS and iPadOS
- App code signing process
- Security of runtime process
- Supporting extensions
- App protection and app groups
- Verifying accessories
- Intro to app security for macOS
- Gatekeeper and runtime protection
- Protecting against malware
- Controlling app access to files
- Secure features in the Notes app
- Secure features in the Shortcuts app
- Services security overview
- Apple ID security
- Managed Apple ID security
- iCloud security overview
- iCloud encryption
- Advanced Data Protection for iCloud
- Security of iCloud Backup
- Account recovery contact security
- Legacy Contact security
- iCloud Private Relay security
- Passcode security overview
- Sign in with Apple security
- Automatic strong passwords
- Password AutoFill security
- App access to saved passwords
- Password security recommendations
- Password Monitoring
- Sending passwords
- Credential provider extensions
- iCloud Keychain security overview
- Secure keychain syncing
- Secure iCloud Keychain recovery
- Escrow security for iCloud Keychain
- Apple Pay security overview
- Apple Pay component security
- How Apple Pay keeps users’ purchases protected
- Card provisioning security overview
- Adding credit or debit cards to Apple Pay
- Payment authorization with Apple Pay
- Paying with cards using Apple Pay
- Contactless passes in Apple Pay
- Rendering cards unusable with Apple Pay
- Apple Card security
- Apple Cash security
- Tap to Pay on iPhone
- Access using Apple Wallet
- Access credential types
- Car key security
- Adding transit and eMoney cards to Apple Wallet
- IDs in Apple Wallet
- iMessage security overview
- How iMessage sends and receives messages
- Secure iMessage name and photo sharing
- Secure Apple Messages for Business
- FaceTime security
- Find My security
- Locating missing devices
- Continuity security overview
- Handoff security
- iPhone cellular call relay security
- iPhone Text Message Forwarding security
- Instant Hotspot security
- Network security overview

TLS security
- IPv6 security
- VPN security
- Secure access to wireless networks
- Wi-Fi privacy
- Bluetooth security
- Ultra Wideband security
- Single sign-on security
- AirDrop security
- Wi-Fi password sharing security
- Firewall security
- Developer kit security overview
- Communication security
- Data security
- Securing routers with HomeKit
- Camera security
- Security with Apple TV
- SiriKit security
- DriverKit security
- ReplayKit security
- ARKit security
- Secure device management overview
- Pairing model security
- MDM security overview
- Configuration profile enforcement
- Automated Device Enrollment
- Activation Lock security
- Managed Lost Mode and remote wipe
- Shared iPad security
- Apple Configurator security
- Screen Time security
- Document revision history
iOS, iPadOS, and macOS support Transport Layer Security (TLS 1.0, TLS 1.1, TLS 1.2, TLS 1.3) and Datagram Transport Layer Security (DTLS). The TLS protocol supports both AES128 and AES256, and prefers cipher suites with forward secrecy. Internet apps such as Safari, Calendar, and Mail automatically use this protocol to enable an encrypted communication channel between the device and network services. High-level APIs (such as CFNetwork) make it easy for developers to adopt TLS in their apps, while low-level APIs (such as Network.framework) provide fine-grained control. CFNetwork disallows SSL 3, and apps that use WebKit (such as Safari) are prohibited from making an SSL 3 connection.
In iOS 11 or later and macOS 10.13 or later, SHA-1 certificates are no longer allowed for TLS connections unless trusted by the user. Certificates with RSA keys shorter than 2048 bits are also disallowed. The RC4 symmetric cipher suite is deprecated in iOS 10 and macOS 10.12 . By default, TLS clients or servers implemented with SecureTransport APIs don’t have RC4 cipher suites enabled and are unable to connect when RC4 is the only cipher suite available. To be more secure, services or apps that require RC4 should be upgraded to use secure cipher suites. In iOS 12.1 , certificates issued after October 15, 2018, from a system-trusted root certificate must be logged in a trusted Certificate Transparency log to be allowed for TLS connections. In iOS 12.2 , TLS 1.3 is enabled by default for Network.framework and NSURLSession APIs. TLS clients using the SecureTransport APIs can’t use TLS 1.3.
App Transport Security
App Transport Security provides default connection requirements so that apps adhere to best practices for secure connections when using NSURLConnection, CFURL, or NSURLSession APIs. By default, App Transport Security limits cipher selection to include only suites that provide forward secrecy, specifically:
ECDHE_ECDSA_AES and ECDHE_RSA_AES in Galois/Counter Mode (GCM)
Cipher Block Chaining (CBC) mode
Apps are able to disable the forward secrecy requirement per domain, in which case RSA_AES is added to the set of available ciphers.
Servers must support TLS 1.2 and forward secrecy, and certificates must be valid and signed using SHA256 or stronger with a minimum 2048-bit RSA key or 256-bit elliptic curve key.
Network connections that don’t meet these requirements will fail unless the app overrides App Transport Security. Invalid certificates always result in a hard failure and no connection. App Transport Security is automatically applied to apps that are compiled for iOS 9 or later and macOS 10.11 or later.
Certificate validity checking
Evaluating the trusted status of a TLS certificate is performed in accordance with established industry standards, as set out in RFC 5280 , and incorporates emerging standards such as RFC 6962 (Certificate Transparency). In iOS 11 or later and macOS 10.13 or later, Apple devices are periodically updated with a current list of revoked and constrained certificates. The list is aggregated from certificate revocation lists (CRLs), which are published by each of the built-in root certificate authorities trusted by Apple, as well as by their subordinate CA issuers. The list may also include other constraints at Apple’s discretion. This information is consulted whenever a network API function is used to make a secure connection. If there are too many revoked certificates from a CA to list individually, a trust evaluation may instead require that an online certificate status response (OCSP) is needed, and if the response isn’t available, the trust evaluation will fail.
Download this guide as a PDF
Looks like no one’s replied in a while. To start the conversation again, simply ask a new question.
online banking security requires Tls1.2. How do I enable it?
iPad Mini Wi-Fi, iOS 9.2.1
Posted on Jun 7, 2018 10:15 AM
Posted on Jun 7, 2018 10:43 AM
There's nothing to do for Safari. Just login to your banking website as usual.
To enable TLS 1.1 and 1.2 in Safari, perform the following steps: 1. There are no options for enabling SSL or TLS protocols. If you are using Safari version 7 or
greater, TLS 1.1 and 1.2 are automatically enabled.
Above information from here > https://www.banknet.gov/entrance/tls-browser-fix.pdf
Similar questions
- disable tls 1.1 We have a client trying to meet new HIPAA compliance requirements, one of which is to use only TLS 1.2 . He has Safari 12.1.2 , which I understand has both TLS 1.1 and TLS 1.2 enabled. How can we disable TLS 1.1, and force him to use 1.2 only? 5127 3
- how do I get encrytion TLS 1.1 or 1.2 onto Safari 11.1.2 how do I get encrytion TLS 1.1 or 1.2 onto Safari 11.1.2 865 1
Loading page content
Page content loaded
Jun 7, 2018 10:43 AM in response to Gramma62
Jun 7, 2018 10:18 AM in response to Gramma62
I suggest you ask your bank. They should be able to provide you with instructions to do that.
Jun 7, 2018 10:46 AM in response to Carolyn Samit
Jun 7, 2018 10:47 AM in response to Gramma62
You're welcome 🙂
Information Technology
Search form.
- Technology Help Desk
- How-To Articles
- IT Services Portal
- Ticket Status
- Feature Articles
- Alerts & Announcements
- Customer Success Stories
- In the News
- IT Events Calendar
- Report a Security Concern
- Accounts & Access
- Data Classification & Compliance
- Security Awareness Training
- Vendor Risk Assessment
- Services by Category
- Software for Faculty
- Software for Staff
- Software for Students
- Software for Research
- IT Training & Development
- On-Demand Learning
- Instructor-Led Training
- Training Content Development
- Tech Ambassadors
- About Pitt IT
- Office of the CIO
- Leadership Team
- IT Vision and Strategy
- Community Engagement
- IT 10-Year Horizon
You are here
Enable support for tls 1.2 or 1.3 on web browsers.
In keeping with security best practices, the University is requiring the use of current web browsers to ensure continued access to University web services—including Pitt Passport .
Older web browsers use out-of-date protocols that do not support modern encryption and contain security vulnerabilities that can be exploited by attackers. Effective July 1, 2021, only web browsers that support versions 1.2 or 1.3 of the Transport Layer Security (TLS) protocol will be permitted to access University web services. Browsers that use TLS version 1.0 or 1.1 will not be supported.
To ensure your web browser supports TLS 1.2 or 1.3, complete the steps below.
Microsoft Edge
TLS 1.2 is automatically enabled in all versions of Microsoft Edge.
Google Chrome
TLS 1.2 is automatically enabled in Google Chrome version 29 or greater.
- Ensure you are using the most recent version of Chrome ...
Apple Safari
TLS 1.2 is automatically enabled in Safari version 7 or greater.
- Ensure you are using the most recent version of Safari ...
Mozilla Firefox
TLS 1.2 is automatically enabled in Firefox version 27 or greater.
- Ensure you are using the most recent version of Firefox ...
To enforce TLS version 1.3 in Firefox, complete the steps below.
1. Open Firefox.
2. In the address bar, type about:config and press Enter .
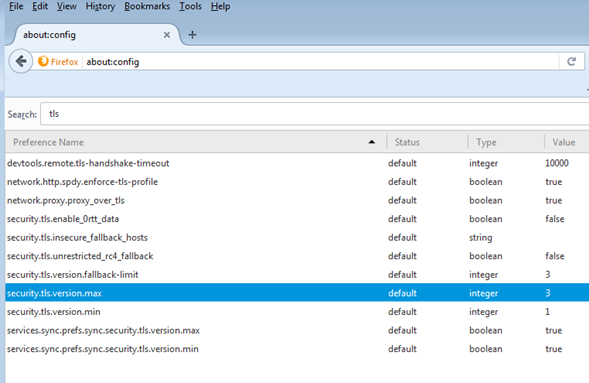
3. In the Search field, enter tls . Find and double click the entry for security.tls.version.max .
4. Set the integer value to 4 to force a maximum protocol of TLS 1.3.

5. Click OK .
6. Close your browser and restart Mozilla Firefox.
Microsoft Internet Explorer
1. Open Internet Explorer.
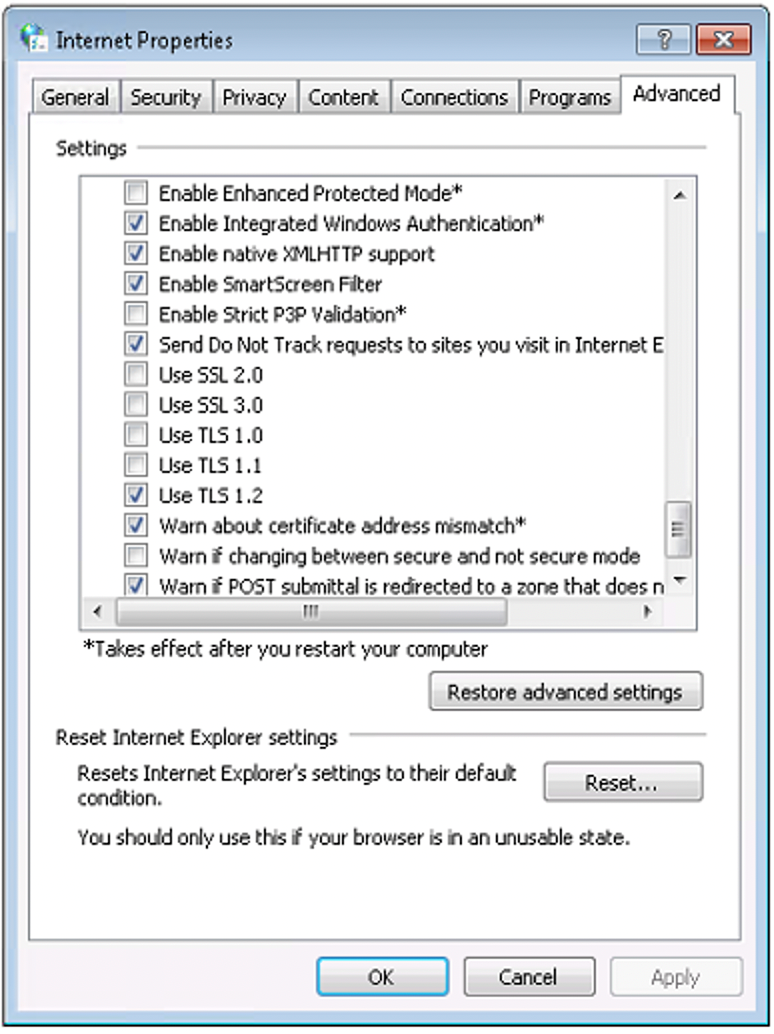
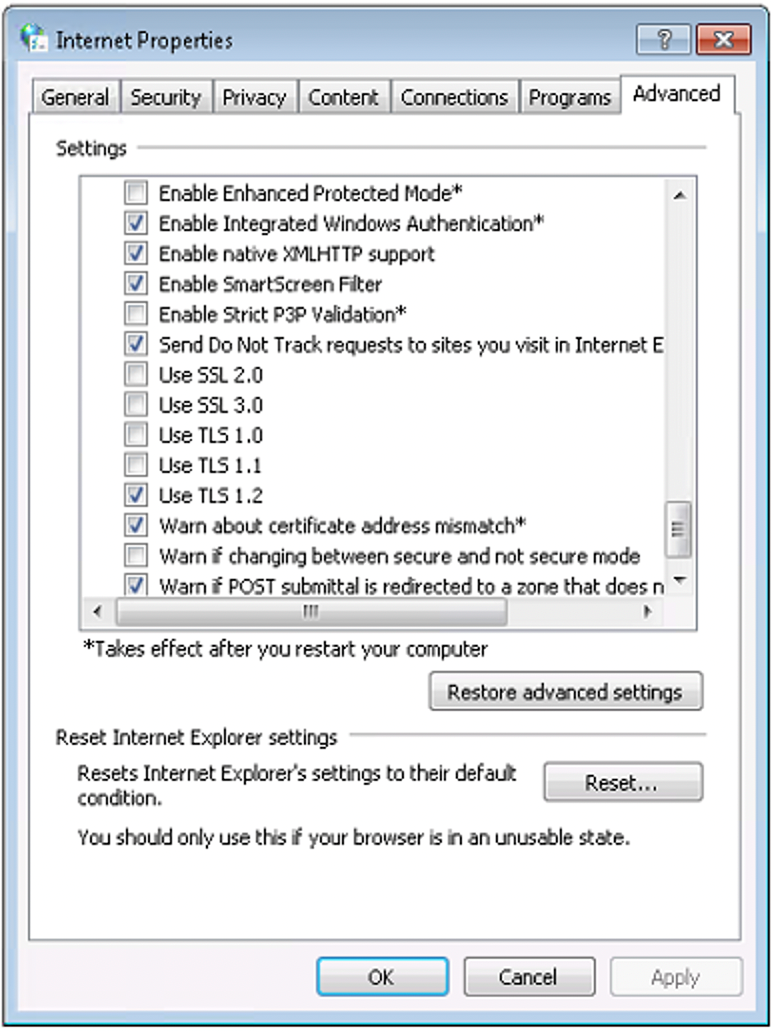
2. From the menu bar, click Tools , then Internet Options , then click the Advanced tab.
3. Scroll down to the Security category and manually check the box next to Use TLS 1.2 .

4. Click OK .
5. Close your browser and restart Internet Explorer.

- Software updates and news
Manually enabling TLS 1.1 and/or TLS 1.2 protocols on web browsers
TLS, short for Transport Layer Security, is an encryption protocol that protects data in transit from one server to another. The encryption protocol deploys whenever a web browser or application transmits data over a network. As of 30 June 2018, the Payment Card Industry (PCI) requires all data processors to withdraw support for the encryption method Transport Layer Security (TLS) version 1.0, as it is no longer regarded as strong ‘cryptography.’
Engaging Networks will disable TLS 1.0 on 1st June 2018 at 1 pm EDT / 6pm BST. Please note that no downtime will be required for the update.
What actions are required?
TLS 1.0 has already been superseded by TLS 1.1 and TLS 1.2. Modern browsers now use the latter methods for processing.
As a day to day user of Engaging Networks, using a modern browser, and (if relevant) as an organisation processing payments on behalf of your supporters, you will see no change after the 1 June 2018 update.
If you are an organisation that has third party providers connecting to Engaging Networks, through APIs, you should confirm that these providers are TLS 1.1 and TLS 1.2 ready.
Some of your supporters might still be running older operating systems and browsers, and if they have not enabled TLS v1.1 and TLS v1.2 under their browser’s settings screen, then Engaging Networks pages will fail to load for them. This is especially true for supporters who may still be using Desktop Internet Explorer versions 8, 9, or 10.
How to enable TLS protocols on older browsers
If you are running an older browser, you need to enable the browser’s TLS 1.1 and/or TLS 1.2 protocols to help with page viewing.
For security, it is always recommended to upgrade your operating system and browser to be inline with industry standards.
For instructions on how to enable these protocols in your older browsers, check the list below:
Microsoft Internet Explorer
Google chrome, mozilla firefox, apple safari.
- Open Internet Explorer
- From the menu bar, click Tools > Internet Options > Advanced tab
- Scroll down to Security category, manually check the option box for Use TLS 1.1 and Use TLS 1.2
- Close your browser and restart Internet Explorer
- Open Google Chrome
- Click Alt F and select Settings
- Scroll down and select Show advanced settings…
- Scroll down to the Network section and click on Change proxy settings…
- Select the Advanced tab
- Close your browser and restart Google Chrome
- Open Firefox
- In the address bar, type about:config and press Enter
- In the Search field, enter tls . Find and double-click the entry for security.tls.version.min
- Set the integer value to 3 to force protocol of TLS 1.3
- Close your browser and restart Mozilla Firefox
- Click Ctrl plus F12
- Close your browser and restart Opera
There are no options for enabling SSL protocols. If you are using Safari version 7 or greater, TLS 1.1 and TLS 1.2 are automatically enabled.
For more details, click here
Was this article helpful?

choose your language

Knowledge Base
Enabling tls 1.2 on web browsers.
Description
To enable TLS 1.2 protocol on web browsers, see the list below.
- Internet Explorer
Google Chrome
Mozilla firefox, apple safari, microsoft internet explorer.
- From the Start Menu > Open ‘Internet Options’ Options > Advanced tab
- Close your browser and restart Internet Explorer
- Close your browser and restart Google Chrome
- Open Firefox
- In the address bar, type about:config and press Enter
- In the Search field, enter tls . Find and double-click the entry for security.tls.version.max
- For security.tls.version.min set the integer value to 3 to force protocol of TLS 1.2
- Close your browser and restart Mozilla Firefox
- Open Opera
- Click Ctrl plus F12
- Scroll down to the Network section and click on Change proxy settings...
- Select the Advanced tab
- Close your browser and restart Opera
There are no options for enabling SSL protocols. If you are using Safari version 7 or greater, TLS 1.2 are automatically enabled.
- From Start Menu > Open ‘Internet Options’ Options > Advanced tab
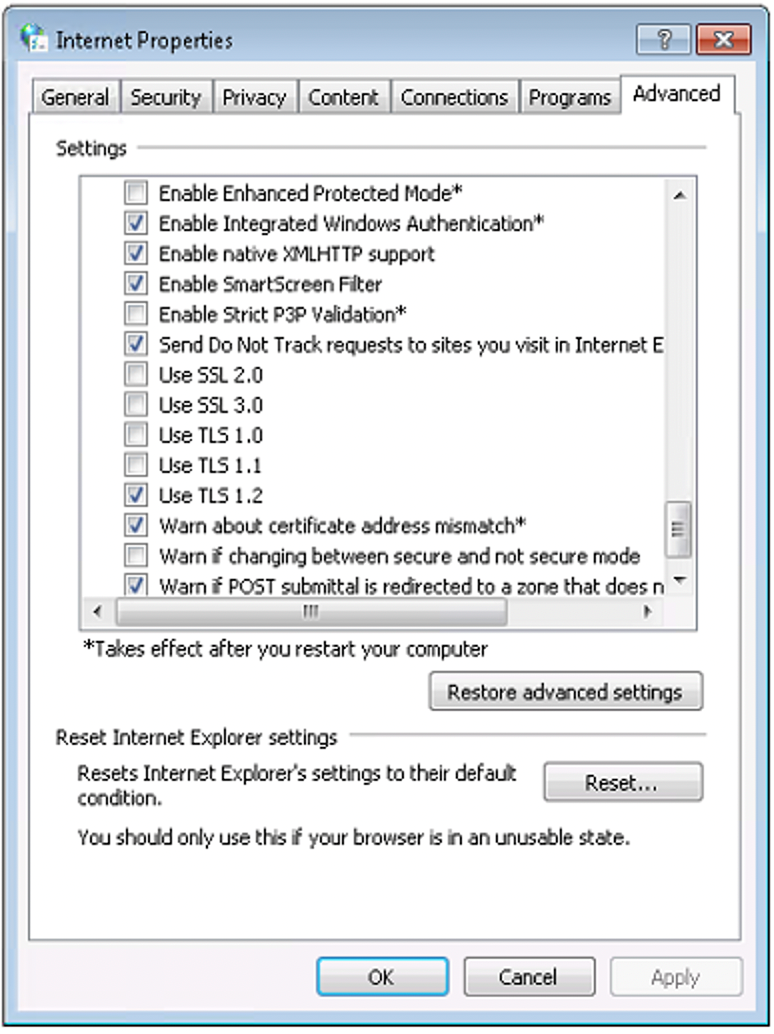
- Close your browser and restart MS Edge

The most-trusted global provider of high-assurance TLS/SSL, PKI, IoT and signing solutions.
- TLS/SSL Support
- PKI Support
- SSL Checker
- Certificate Utility
- Generate CSR
- Report Certificate Misuse
- Compare Certificates
- TLS/SSL Certificates
- Pro TLS/SSL Certificates
- Multi-Domain SSL
- Wildcard Certificates
- Document Signing
- Code Signing
- CertCentral
- DigiCert® Trust Lifecycle Manager
- DigiCert® IoT Trust Manager
- DigiCert® Software Trust Manager
- DigiCert® Document Trust Manager
- Solutions Overview
- DigiCert ONE
© 2022-2024, DigiCert, Inc. All rights reserved.
- Identity & Security
- Engineering
- Announcements
- Try Auth0 For Free Talk To Sales

The TLS Handshake Explained
Transport Layer Security (TLS) is the cryptographic protocol behind pretty much any computer network used today: from web browsing to email, APIs, and VoIP. But how exactly does it work?

March 07, 2023
SSL vs. TLS
SSL, or Secure Sockets Layer, is the predecessor to TLS. It was a cryptographic protocol developed by Netscape in 1994, but since it had serious flaws, it was never released to the public. SSL 2.0 was released publicly one year later, in 1995, but it, too, was found to have serious flaws. Finally, SSL 3.0 was rebuilt from the ground up and released in 1996.
Microsoft, who had its own version of the protocol, and Netscape agreed to hand over the project to the Internet Engineering Task Force (IETF) and make it an open standard. As part of the deal, the name was changed to TLS, Transport Layer Security, to signify that it no longer had ties with Netscape.
The first upgrade to SSL 3.0 was published in 1999 in RFC 2246 as TLS 1.0. Tim Dierks, the editor of RFC 2246, has said in his blog that TLS 1.0 was really SSL 3.1, but they changed the name “so it wouldn’t look the IETF was just rubberstamping Netscape’s protocol.” Indeed, if you look at RFC 2246, it says:
This document describes TLS Version 1.0, which uses version { 3, 1 }. Version value 3.1 is historical: TLS version 1.0 is a minor modification to the SSL 3.0 protocol, which bears the version value 3.0.
TLS became the standard of encryption and authentication over computer networks, and it’s still being used today. The most recent version of the protocol is TLS 1.3, which was released in August 2018.
What is the difference between SSL and TLS?
SSL hasn’t been updated since its release in 1996, and it was deprecated in 2015 in RFC 7568 . Most modern browsers disable it by default or don’t support it outright anymore.
Despite this, because of the association between the two, many people still use the term SSL when they really mean to say TLS. Vendors typically use the same terms their target customers use to facilitate messaging, so their marketing collateral generally contains terms such as “SSL/TLS” or “SSL,” even though SSL is deprecated.
We now know that SSL and TLS are different things, but for the remainder of this article, SSL will be used interchangeably with TLS to match its everyday usage.
Why SSL/TLS Was Created
For two computers to communicate with each other, they must perform a set of agreed-upon operations in a specific order. A protocol is what dictates those operations. The HTTP protocol is the protocol that web servers and clients use to establish a connection and communicate with each other through the Internet.
It works roughly as follows:
- The server listens for new connections on port 80
- The client connects to the server, and this starts a chain of operations as set forth by the HTTP protocol
- The client sends a GET request to the server; the server receives the request, processes it, then sends back a response: headers and index.html, plus other content it might need to serve (CSS files, JavaScript files, cookies, etc.) for the client to render the content correctly.
This works to distribute content between two remote computers, but there is a problem: HTTP was intended to expand the local knowledge management tools throughout the multiple computers at CERN in the late 1980s, so it was designed as a clear text protocol.
Because it’s clear text, a malicious actor could insert themselves between client and server and potentially read sensitive information, such as credit card numbers or passwords, or they could intercept the client’s requests and serve back malicious files pretending to be server.
As the Internet evolved and the number of sensitive information flying around increased exponentially, an encryption layer sitting below HTTP was necessary. However, this is a bit tricky: if a bad actor can “listen in” the conversation between client and server while the connection is unencrypted, how can they exchange encryption keys securely?
One option would be for the two parties to create a public-private key pair and send over the public key pair to the other party, so they can use that to encrypt their packet before sending them over the wire.
The problem with this is that asymmetric (public-key) cryptography is much slower than symmetric cryptography.
The "strength" of asymmetrical cryptography relies on modular arithmetic, mathematical operations that are very hard to do in the opposite direction. The numbers used in these operations need to be big enough to provide the necessary security, but performing arithmetic with very large numbers can be taxing on a CPU.
Symmetric cryptography, on the other hand, works differently and does not suffer from this problem. On top of that, most devices have AES instruction sets integrated into their CPUs to speed up AES operations, making AES encryption have almost zero overhead on modern devices.
The TLS protocol gets around this issue by using asymmetric cryptography to exchange keys at the beginning and then switch to symmetric keys (“sessions keys”) from then on in a process known as the TLS handshake.
TLS handshakes
The exact steps of the TLS handshake will depend on which TLS version is supported by the client and server, as well as which parameters they are set to use.
Since most modern browsers still support TLS 1.2 and a lot of websites still use TLS 1.2 (according to a paper published by Syed-Winkler , as of February 2021, TLS 1.3 is supported by 42.9% of surveyed websites, while TLS 1.2 is supported by 99.3%), we will talk about TLS 1.2 first and then discuss how TLS 1.3 differs from 1.2.
The TLS 1.2 handshake
TLS 1.2 can be configured to use many key exchange algorithms, and among them, the most well-known and widely used is the RSA key exchange algorithm. Let’s go over how the RSA algorithm works in TLS 1.2, then talk about how the process differs in TLS 1.3 with the Diffie-Hellman (DH) key exchange algorithm.
The RSA key exchange works roughly as follows in TLS 1.2:
- Server listens for new connections on port 443.
- Client connects to port 443 and initiates the handshake process with a ClientHello message to the server. This message contains the TLS versions and cipher suites the client supports and a 32-byte random number known as Client Random.
- Server says “hello” back with a ServerHello message. The server selects a cipher and the TLS version from the list provided by the client, then generates a different 32-byte random number known as Server Random and sends it all back along with the server’s own SSL certificate.
- Client uses the SSL certificate to verify the server’s identity. SSL certificates contain a public key generated by the server and a digital signature signed with the private key of a trusted third party known as a certificate authority (CA). Most web browsers and operating systems come bundled with public keys from trusted CAs, which are used to verify that the CA issued the certificate.
- The client verifies the server has the matching private key to the certificate through ClientKeyExchange. The client generates the pre-master secret (a 48-byte random number) and encrypts it with the server’s public key obtained from the certificate. If the server is the true owner of the certificate, it must be able to decrypt the message and obtain the original pre-master secret.
- Server decrypts the pre-master secret. Now both the server and client have the pre-master secret, the Server Random, and the Client Random. They can use that to derive the master secret using the previously agreed cipher and arrive at the same (symmetric) key, which will become the session key once both parties verify their keys match.
- Client sends a ChangeCipherSpec message. This indicates that the client is ready to create the session key and start communicating through an encrypted tunnel using that key.
- Client proves to server it has the correct keys. The client hashes all handshake records up to that point, encrypts them with the session key, and sends them to the server. If the server generates the correct key, it will be able to decrypt that message and verify the record hashes (which the server can independently generate).
- Server proves to the client that it has the correct keys. The server does the same thing and sends it to the client.
- A secure connection is established. If both keys match, the TLS handshake is complete.
Problems with TLS 1.2
TLS 1.2 left a lot of its configuration parameters up to the users, which often resulted in bad choices (the old security adage of “among too many options, the worst one will be chosen”).
Additionally, in the name of backward compatibility, TLS 1.2 also allowed old, insecure ciphers to be used. (TLS 1.2 itself was released in 2008.) As time passed, it became more prone to attacks as vulnerabilities in older cipher or versions of TLS were discovered.
On top of all that, the RSA key exchange has a few weaknesses:
- The same public-private key pair is used both to authenticate the server and to encrypt the pre-master secret (item #5 above). If an attacker obtains the private key, they will be able to re-generate the session keys and be to decrypt the entire session.
- There is no Perfect Forward Secrecy (PFS). Since the server’s private key doesn’t change, an attacker might record and store encrypted data for years, hoping to decrypt it years down the line if the server’s private key is ever leaked or compromised.
- Performance. It’s necessary to make two round trips between the client and server until the session key is established.
To address these problems, the IETF began developing TLS 1.3 in 2013 and finally released it to the public in August 2018.
What changed in TLS 1.3
In practice, the main differences between TLS 1.3 and 1.2 are:
- Shorter handshake
- Only supports key exchange algorithms with perfect forward secrecy (PFS), such as ephemeral Diffie-Hellman
- Support for 0-RTT (Zero Round Trip Time) resumption
This represents a bit of a paradigm change in TLS 1.3: shifting the focus from user configurability and backward compatibility to security by being more opinionated.
This allowed the designers to create a shorter handshake (by restraining DH as the only key exchange algorithm) but also prevented developers from choosing insecure options by restricting the number of options available in the first place.
For example, while it was technically possible to use DH as the key exchange method in TLS 1.2, the participants were responsible for setting the DH parameters. Picking the right parameters is crucial to make sure the DH exchange is secure, as some parameters can be trivially broken.
In 2015, security researchers published a paper describing how the WeakDH attack, which affected 8.4% of the top 1 million domains at the time, could trick servers into using small (insecure) DH parameters, enabling adversaries to decrypt data transmitted between client and server.
TLS 1.3 makes it impossible to use anything but a set of DH parameters that are believed to be secure.
The TLS 1.3 handshake
Because there are significantly fewer options for the client and server to agree on, the TLS 1.3 handshake is much simpler:
- Client connects to port 443 and initiates the handshake process with a ClientHello message to the server. Since the list of cipher suites was vastly reduced in TLS 1.3 (from 37 to 5), the client assumes the server is going to use one of the five. It proactively calculates a key pair for each of the cipher suites and sends it to the server along with the protocol version.
- Server calculates the key session. With the client’s key share, the server is able to generate the session key.
- Server says “hello” back with a ServerHello message. The server generates its own key share and sends it over to the client, so it also can generate the session key, along with the server’s encrypted SSL certificate (using the session key created on #3).
- Client generates master secret and a secure connection is established. The client receives the server’s key share and calculates the session key. It decrypts and verifies the server’s certificates, and if everything is good, the handshake is complete.
Note that there are two different public-private key pairs on an ephemeral DH exchange: the first is the ephemeral pair, created every time client and server establish a connection, which guarantees forward secrecy. The second pair, embedded on the SSL certificate, is used for authentication and doesn’t change.
Given that a new key is generated for every session, this feature guarantees PFS. If the encryption keys are compromised at a later date, the leaked key will only be able to decrypt the specific session to which it corresponds; all the prior sessions are still safe. As a result, large-scale storage of data transmitted between server and client is rendered worthless.
How Auth0 Can Help
The temptation to intercept, undermine, and circumvent encryption has never been stronger. Cybercriminals are working to find ways to get around the issues that strong encryption presents due to the volume of valuable information that is sent between computers today.
While this rarely results in direct assaults against cryptographic algorithms or protocols, it frequently prompts attackers to devise novel methods of intercepting or capturing information. With these threats ever present, it is more crucial than ever to focus on maintaining strong and up-to-date implementations of effective encryption protocols.
Some applications are still running TLS versions older than 1.2, and others are still running the original SSL protocol. If yours is one of them, you should consider upgrading it immediately. Auth0 supports both TLS 1.2 and TLS 1.3 and can help you keep your applications secure.
You are using an outdated browser. Please upgrade your browser to improve your experience.
Apple deprecates TLS 1.0 and 1.1 with iOS 15, macOS 12, more

TLS 1.0 and 1.1 has been deprecated in iOS 15 , iPadOS 15 , watchOS 8 , macOS 12 and tvOS 15 and support for the protocols will be removed in future releases, Apple said in a post to its developer website on Tuesday.
The company first announced plans to transition away from early versions of TLS in 2018 , saying Safari would move to TLS version 1.2 and 1.3 in 2020. Those changes were implemented in initial betas of iOS 13.4 and macOS 10.15.4.
Explaining the shift in 2018, Apple software engineer Christopher Wood described TLS as a critical internet security protocol for protecting web traffic as it moves between clients and servers. Despite handling sensitive data, legacy versions date back to 1999.
As noted by Apple today, the Internet Engineering Task Force (IETF) deprecated TLS 1.0 and 1.1 as of March 25, 2021. The IETF approved the next iteration of TLS, version 1.3, in 2018.
Apple urges developers to build in support for TLS 1.3, calling it "faster and more secure." Apps that currently use TLS 1.0 or 1.1 are asked to transition to TLS 1.2 or later. Developers who have enabled App Transport Security (ATS) on all connections do not need to make additional changes to their app, as the feature requires connections secured with modern TLS certificates.
BleepingComputer reported on the change earlier today .
There are no Comments Here, Yet
Top stories.

Amazon drops Apple's M3 MacBook Air to record low $989

Retro gold rush: these emulators are coming to the App Store soon

The Worst of WWDC - Apple's biggest missteps on the way to success

Apple's generative AI may be the only one that was trained legally & ethically

Arizona TSMC facility continues to fight cultural battles, rising costs & logistical hurdles

New iPad Air & iPad Pro models are coming soon - what to expect
Featured deals.

Save up to $350 on every Apple M3 MacBook Pro, plus get up to $80 off AppleCare
Latest comparisons.

M3 15-inch MacBook Air vs M3 14-inch MacBook Pro — Ultimate buyer's guide

M3 MacBook Air vs M1 MacBook Air — Compared

M3 MacBook Air vs M2 MacBook Air — Compared
Latest news.
Some users are randomly getting locked out of their Apple ID accounts
Overnight, a notable portion of iCloud users were getting logged out of their accounts across all of their devices, and the only way back in was to perform a password reset.

Apple said to have restarted discussion for OpenAI integration into iOS 18
A report suggests that Apple is still looking across the spectrum of AI providers for iOS 18, with OpenAi again in conversations with the iPhone maker.

Apple is allowing emulators to be submitted to the App Store. Here's what's on the way so you can play your favorite retro games on your iPhone.

How to connect to FTP servers in macOS using modern apps
File Transfer Protocol is an older networking protocol for transferring files to network servers. Here's how to use it on your Mac.

Apple finally pulls generative AI nude apps from the App Store
Apple has removed apps from the App Store that claimed to make nonconsensual nude imagery, a move that demonstrates Apple is now more willing to tackle the hazardous app category.


ByteDance would rather shut down US TikTok than sell it
TikTok owner ByteDance reportedly will not sell to a US firm if it is unable to convince a court to overturn President Biden's day-old law forcing a sale or ban.

Apple's recently released M3 MacBook Air has dropped to an all-time low of $989 at Amazon while supplies last.

Unistellar Odyssey Pro review: Unlock pro-level astronomy with your iPhone from your backyard
Unistellar's Odyssey Pro smart telescope delivers amazing results even from a light-polluted backyard — and we have the photographic evidence to prove it.

WWDC is Apple's annual backdrop for its most important software and hardware announcements. It has also unintentionally launched some of Apple's biggest flops.

FCC votes to restore net neutrality protections in the United States
In an entirely expected move, the Federal Communications Commission has voted to reinstate net neutrality protections in the United States.

Apple bids farewell to Frank Casanova after pivotal 36-year tenure
After nearly four decades at Apple, Frank Casanova, the Senior Director of Product Marketing who recently spearheaded the launch of the Vision Pro headset, has retired.
Latest Videos

All of the specs of the iPhone SE 4 may have just been leaked

When to expect every Mac to get the AI-based M4 processor
Latest reviews.

Ugreen DXP8800 Plus network attached storage review: Good hardware, beta software

Espresso 17 Pro review: Magnetic & modular portable Mac monitor

{{ title }}
{{ summary }}
- a. Send us an email
- b. Anonymous form
- Buyer's Guide
- Upcoming Products
- Tips / Contact Us
- Podcast Instagram Facebook Twitter Mastodon YouTube Notifications RSS Newsletter
Apple Ending Safari Support for TLS 1.0 and 1.1 in March 2020
Ahead of the planned deprecation, Apple recommends apps adopt TLS 1.2, which offers "security fit for the modern web." Upgrading from TLS 1.0 and 1.1 provides the following benefits, according to Apple:
- Modern cryptographic cipher suites and algorithms with desirable performance and security properties, e.g., perfect forward secrecy and authenticated encryption, that are not vulnerable to attacks such as BEAST. - Removal of mandatory and insecure SHA-1 and MD5 hash functions as part of peer authentication. - Resistance to downgrade-related attacks such as LogJam and FREAK.
TLS 1.2 is the standard on Apple platforms and already represents 99.6 percent of connections made from Safari. Apple says TLS 1.0 and 1.1 account for less than 0.36 percent of all connections.
Other browsers, including Firefox, Chrome, and Microsoft's Edge, are also planning to drop TLS 1.0 and 1.1 support starting in early 2020.
Get weekly top MacRumors stories in your inbox.
Top Rated Comments
Curious to know what would happen to the small amount of apps/pages that don't update to TLS 1.2? Will they just stop working?
Guess I’ll be stuck using ancient versions of chrome/Firefox for a while longer. I get the reasons, but there are use cases in the enterprise realm where we need to connect to ancient internal systems. It’s not always easy upgrading a server due to various compatibility requirements.
Popular Stories

iOS 18 Rumored to Add These 10 New Features to Your iPhone
Apple Releases Open Source AI Models That Run On-Device

Apple Announces 'Let Loose' Event on May 7 Amid Rumors of New iPads

Best Buy Introduces Record Low Prices on Apple's M3 MacBook Pro for Members

Apple ID Accounts Logging Out Users and Requiring Password Reset

Apple's Regular Mac Base RAM Boosts Ended When Tim Cook Took Over
Next article.

Our comprehensive guide highlighting every major new addition in iOS 17, plus how-tos that walk you through using the new features.

App Store changes for the EU, new emoji, Podcasts transcripts, and more.

Get the most out your iPhone 15 with our complete guide to all the new features.
A deep dive into new features in macOS Sonoma, big and small.

Revamped models with OLED displays, M3 chip, and redesigned Magic Keyboard accessory.

Updated 10.9-inch model and new 12.9-inch model, M2 chip expected.

Apple's annual Worldwide Developers Conference will kick off with a keynote on June 10.

Expected to see new AI-focused features and more. Preview coming at WWDC in June with public release in September.
Other Stories

2 days ago by Tim Hardwick

2 days ago by Joe Rossignol

2 days ago by MacRumors Staff

3 days ago by Joe Rossignol

4 days ago by Tim Hardwick

- Subscribe by RSS
System requirements for TLS 1.2 for Mac users
- Last updated
- Save as PDF
- Product: RefWorks
From June 1, 2021, Write-n-Cite will support TLS 1.2 only and will not support earlier versions. Refer to the flowchart or table below for details on checking if your system supports TLS 1.2.
Make sure you meet requirements A, B and C.
System requirements for Windows users: refer here.
The numbers in the flowchart refer to the numbers in the table below it and provide additional details.
For any questions please refer to your RefWorks administrator or to RefWorks Support .
How to check if my Mac supports TLS 1.2: Flowchart
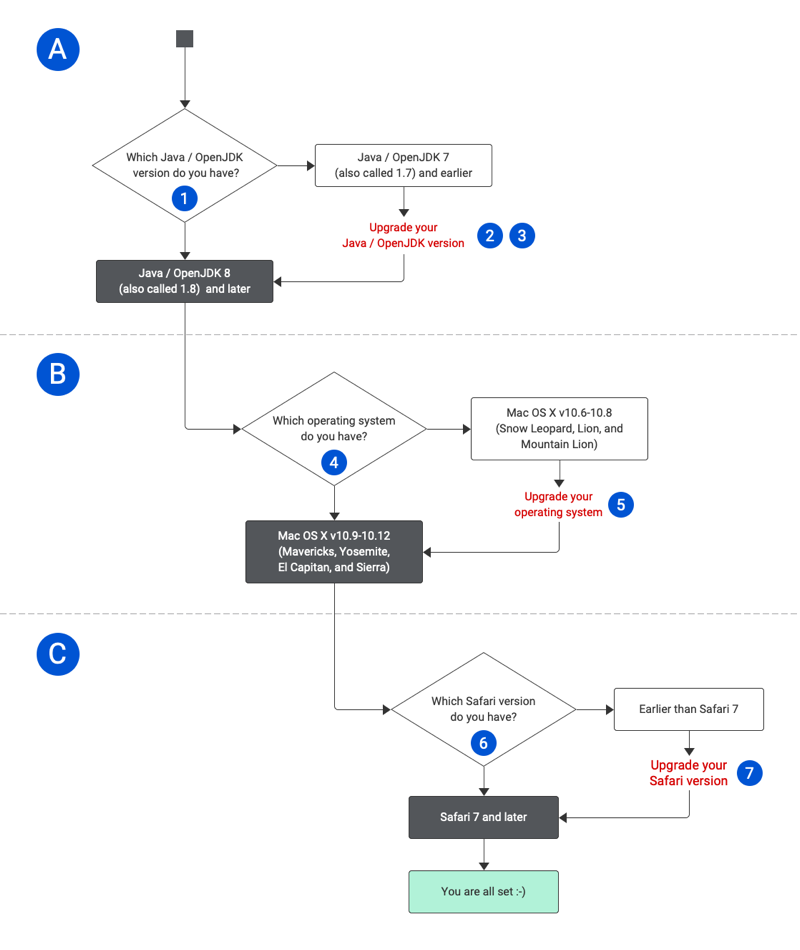
How to check if my Mac supports TLS 1.2: Table
- Article last edited: 11-May-2021
DialogTech is now Invoca. Learn more about the Invoca platform →
Enabling TLS 1.2 on Web Browsers
Apr 13, 2021 • knowledge, information.
Please follow the instructions below to enable TLS 1.2 protocol on web browsers.
Microsoft Internet Explorer
Microsoft Edge
- Google Chrome
Mozilla Firefox
Apple Safari
Note: If you are using a Mac computer, you will need to be on OS X 10.9 or above. No additional updates to the browser settings will be needed as long as they are up to date. For PC browsers follow the instructions below. Note that you have to be on Windows Vista or above to be able to enable TLS 1.2. Windows XP and Server 2003 don't support TLS 1.2.
- Open Internet Explorer
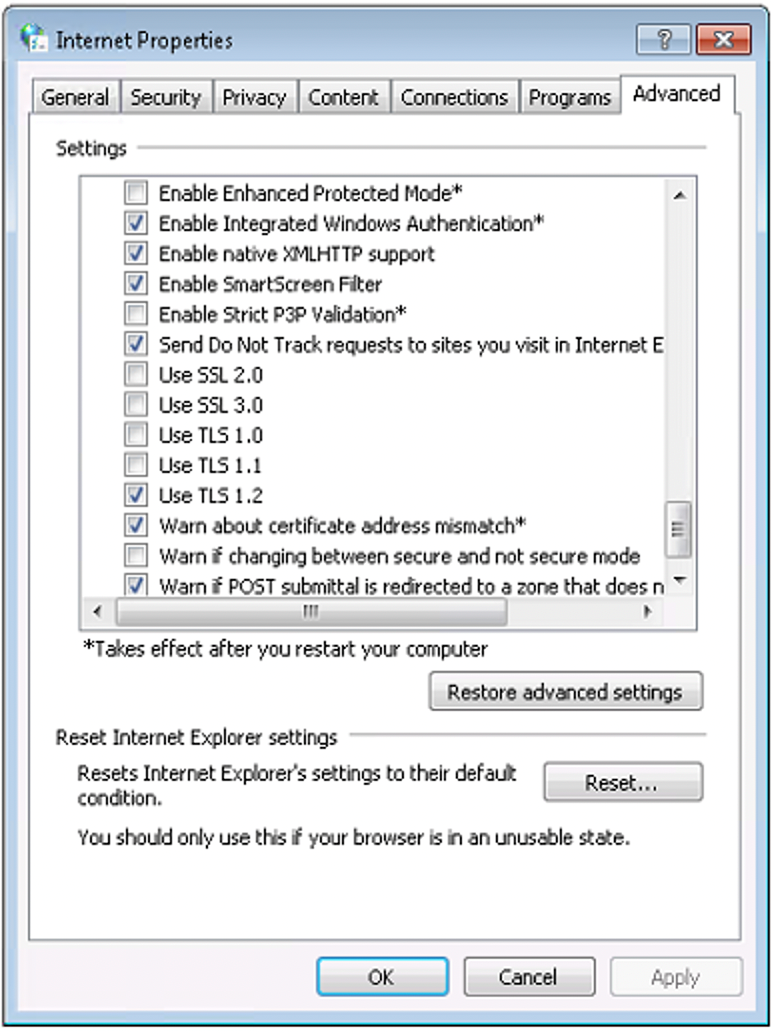
- From the menu bar, click Tools > Internet Options > Advanced tab
- Scroll down to Security category, manually check the option box for Use TLS 1.2
- Click OK
- Close your browser and restart Internet Explorer
- In the Windows menu search box, type Internet options .
- Under Best match , click Internet Options .
- In the Internet Properties window, on the Advanced tab, scroll down to the Security section.
- Check the User TLS 1.2 checkbox.
- Click OK .
- Close your browser and restart Microsoft Edge browser.
Google Chrome Note: Chrome 81 and later support and activate TLS 1.2 by default. Follow the instructions below if you have an earlier version.
- Open Google Chrome
- Click Alt F and select Settings
- Scroll down and select Show advanced settings...
- Scroll down to the System section and click on Open proxy settings...
- Select the Advanced tab
- Close your browser and restart Google Chrome
- Open Firefox
- In the address bar, type about:config and press Enter
- In the Search field, enter tls . Find and double-click the entry for security.tls.version.min
- Set the integer value to 3 to force protocol of TLS 1.2 to be the default.
- Close your browser and restart Mozilla Firefox
There are no options for enabling SSL protocols. If you are using Safari version 7 or greater, TLS 1.2 is automatically enabled.
Related Articles
- Number of Views 727
- Number of Views 470
- Number of Views 243
- Number of Views 2.94K
- Number of Views 3.15K
- System Status
- Customer Support
- (888) 988-4201 (ext 2) M–F 7:30 a.m. – 6 p.m. (CST)
How to disable TLSv 1.0, 1.1, 1.3 and enable only TLSv 1.2 using NSURLSession API
I have issue regarding disable 1.0,1.1 and 1.3.
On our server side we enabled only TLS 1.2 only so I need to disable other all version.
Please check below code.
let request: NSMutableURLRequest = createRequest(url,apiType: apiType, parameters: parameters, body: body as [String : AnyObject]?, headers: PLUtility.getUnwrappedValue(headers),requestType:requestType!)
let configuration = URLSessionConfiguration.default
configuration.tlsMaximumSupportedProtocol = SSLProtocol.tlsProtocol12
configuration.timeoutIntervalForRequest = 30 /
configuration.requestCachePolicy = .reloadIgnoringLocalCacheData
configuration.urlCache = nil
SSLCipherSuite : Ciphers[] = [
TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256,
TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384
Here, I added maximum and min support protocol version TLSv1.2 only but still it is working in TLSv1.0, 1.1, 1.3
Can you please let me know how can I restrict other TLS version expect TLSv1.2
Please let me know how can I pass CipherSuite in Swift ?
can you provide reference url or snippet code.
Kindly let me know if any query.
Thank you in advance.
Accepted Reply
Just as a reminder, TLS protocol negotiation works as follows:
In the Client Hello message, the client sends the server the maximum TLS version it supports and the list of cypher suites it supports.
The server looks at those and picks its preferred TLS version and cypher suite, sending that back to the client in the Server Hello message. Alternatively, if there’s no choice that’s acceptable to the server’s security policy, the server fails the connection.
The client checks the choice returned by the server against the client’s security policy. If it’s unacceptable, the client fails the connection.
I’m confused. If your server only supports TLS 1.2, why do you care what TLS version iOS requests? As long as iOS supports TLS 1.2, it doesn’t matter what iOS tries to negotiate. Your server will always choose TLS 1.2.
Likewise for cypher suites. If the server requires that clients use a specific set of cypher suites, configure your server so that it only negotiates those cypher suites.
Server security policy has to be enforced on the server because enforcing it on the client is pointless: You can’t be guaranteed that only your client is connecting to the server.
Share and Enjoy — Quinn “The Eskimo!” Apple Developer Relations, Developer Technical Support, Core OS/Hardware
Thanks for reply Please let know how to set cypher suites in NSURLSession.Please can you provide snippet of the code.
Please let know how to set cypher suites in NSURLSession .
As before, if you care about security then you need to enforce that on the server. You should enable ATS in your client, which means the client will only use cypher suites that are generally considered secure, and thus configure your server to choose the most secure of the ones offered by the client.
Eskimo I have added the below keys in the info.plist.These keys working fine in iOS 11.0 but its not working on iOS 9 and iOS 10.Please let me know the on which iOS version these keys working. 1.NSIncludesSubdomains = NO 2.NSExceptionRequiresForwardSecrecy = NO 3.NSExceptionMinimumTLSVersion = 1.0 4.NSExceptionAllowsInsecureHTTPLoads = YES Thanks Manjunatha Kaliwal
All of these keys are supported by all versions of App Transport Security (ATS), that is, iOS 9 and later. As to what’s going wrong in your case, it’s hard to say because you’ve not given any information about what you expect the keys to do.
And consider TLS 1.3 compatibility on server as soon as possible
Firefox, Chrome, Safari and Edge Dropping TLS 1.0, 1.1

Apple , Google , Microsoft and Mozilla all announced today that they will disable TLS versions 1.0 and 1.1 in their respective browsers by default by the first half of 2020. The TLS protocol is what browsers, instant messengers and even email servers primarily use to secure communications.
TLS 1.0, 1.1 Deprecated
Over the past few years, we’ve seen new attacks that exploit weaknesses in the design of the TLS 1.0 and TLS 1.1 protocols and algorithms that were used alongside them. These attacks include BEAST , which allows malicious actors to steal the TLS authentication tokens, Logjam and FREAK , which allow attackers to downgrade the security of a connection to a server, as well as insecure hash functions, such as MD5 and SHA-1.
In addition to all of this, the TLS 1.2 protocol is more than a decade old, so both browsers and web developers have little excuse not to use it by now. Earlier this year, the IETF also finalized the TLS 1.3 specification , which further streamlines and upgrades the TLS protocol to be stronger and less easy to break cryptographic algorithms.
What Is the TLS Protocol?
The TLS (stands for Transport Layer Security) protocol is an upgrade to the previously used Secure Sockets Layer (SSL) protocol. Netscape invented SSL because it realized that at least some uses of the internet required secure communications over computer networks.
Netscape kept SSL 1.0 private because it later learned it was deeply flawed. The company made SSL 2.0 public in 1995, but outside security researchers proved soon afterwards that it also had many flaws. In 1996, cryptographer Paul Kocher together with Netscape released version 3.0 of SSL, on top of which TLS 1.0 was developed in 1999. TLS 1.1 came in 2006 and TLS 1.2 in 2008.
Chrome 72 will stop supporting TLS 1.0 and 1.1 in the first half of next year, while Apple’s Safari, Mozilla's Firefox and Microsoft ’s Edge and Internet Explorer 11 browsers will drop support for the two protocol versions a year later, in the first half of 2020.
Stay on the Cutting Edge
Join the experts who read Tom's Hardware for the inside track on enthusiast PC tech news — and have for over 25 years. We'll send breaking news and in-depth reviews of CPUs, GPUs, AI, maker hardware and more straight to your inbox.

Microsoft is working on a RAM limit slider for its Edge Browser, to prioritize memory-intensive applications, PC games
Google releases Chrome for Windows on Arm ahead of Snapdragon X Elite launch
Museum criticizes Microsoft for 'mutilated' MS-DOS 4 open source release — posting on 'stupid' git blamed for the buggy blunder
- Co BIY Do users or developers need to do something in response to this change ? Will most people even notice? Article seems to be a paragraph short. Reply
- Dave_135 Nice Article if your Windows 10 User. But I for 1 think Windows 10 Sucks totally! We Have 3 Computers in this house, My Desktop, called the Video Editing Beast, It has Linux Mint 19 Tara and Windows 7 Pro, then there is the Laptop Hooked to our HD TV, I runs Linux Mint 18.3 Cinnamon and Windows 10. Then we have a Laptop set on a Folding wooden table, it is older HP Model, 32 Bit and I have it running Linux Mint 19 Tara. Usage on all 3 machines on the desktop, Linux Mint gets used about 80% of the time, Windows the rest, on the TV Computer, windows gets about 70% and Linux mint gets the rest. And HP laptop, since Linux Mint 19 Tara has came out, that is all it runs, when I got it had Windows 8 running on it, that was worse that Windows 10. But Windows 10 is still the worst Operating System ever made in My Opinion. The update procedure is nuts as compared to Linux Mint. Updating A Windows 10 computer takes about 20 to 30 minutes of time, Linux mint, I may Install updates 3 times a day and it does not effect my workflow. Reply
- mdarrish DAVE-135: Windows 10 is ugly and many aspects of it indeed suck. M$ has been on a downhill slide since Windows 8. However, Windows ME (ironically named Millenium Edition), sucked equally as much as 10, IMHO. Reply
- cryoburner But... This article has nothing to do with Windows. >_> Reply
- hannibal Those who has web Pages has to upgrade them so that They Are not using TLS 1.0 or 1.1 or their webpages can not be Viewed any more in the future. To the customers, no need to do anything unless you favorite websites stop from being available. Then you have to roll back to old webbrowser to see those Pages! Reply
- stdragon For 99.99% of the population out there, this is a non-issue. But for those that have to support vendor server-side and appliance applications that requires HTTPS administration, it's going to suck...badly. Basically that translates to using an older version of a browser until management can cough up the money to supply IT with a workable budget to upgrade said back-end services. Reply
21405390 said: Do users or developers need to do something in response to this change ? Will most people even notice? Article seems to be a paragraph short.
- View All 7 Comments
Most Popular
This browser is no longer supported.
Upgrade to Microsoft Edge to take advantage of the latest features, security updates, and technical support.
Solving the TLS 1.0 Problem, 2nd Edition
- 7 contributors
This document presents the latest guidance on rapidly identifying and removing Transport Layer Security (TLS) protocol version 1.0 dependencies in software built on top of Microsoft operating systems, following up with details on product changes and new features delivered by Microsoft to protect your own customers and online services. It is intended to be used as a starting point for building a migration plan to a TLS 1.2+ network environment. While the solutions discussed here may carry over and help with removing TLS 1.0 usage in non-Microsoft operating systems or crypto libraries, they are not a focus of this document.
TLS 1.0 is a security protocol first defined in 1999 for establishing encryption channels over computer networks. Microsoft has supported this protocol since Windows XP/Server 2003. While no longer the default security protocol in use by modern OSes, TLS 1.0 is still supported for backwards compatibility. Evolving regulatory requirements as well as new security vulnerabilities in TLS 1.0 provide corporations with the incentive to disable TLS 1.0 entirely.
Microsoft recommends customers get ahead of this issue by removing TLS 1.0 dependencies in their environments and disabling TLS 1.0 at the operating system level where possible. Given the length of time TLS 1.0 has been supported by the software industry, it is highly recommended that any TLS 1.0 deprecation plan include the following:
Code analysis to find/fix hardcoded instances of TLS 1.0 or older security protocols.
Network endpoint scanning and traffic analysis to identify operating systems using TLS 1.0 or older protocols.
Full regression testing through your entire application stack with TLS 1.0 disabled.
Migration of legacy operating systems and development libraries/frameworks to versions capable of negotiating TLS 1.2 by default.
Compatibility testing across operating systems used by your business to identify any TLS 1.2 support issues.
Coordination with your own business partners and customers to notify them of your move to deprecate TLS 1.0.
Understanding which clients may no longer be able to connect to your servers once TLS 1.0 is disabled.
The goal of this document is to provide recommendations which can help remove technical blockers to disabling TLS 1.0 while at the same time increasing visibility into the impact of this change to your own customers. Completing such investigations can help reduce the business impact of the next security vulnerability in TLS 1.0. For the purposes of this document, references to the deprecation of TLS 1.0 also include TLS 1.1.
Enterprise software developers have a strategic need to adopt more future-safe and agile solutions (otherwise known as Crypto Agility) to deal with future security protocol compromises. While this document proposes agile solutions to the elimination of TLS hardcoding, broader Crypto Agility solutions are beyond the scope of this document.
The Current State of Microsoft's TLS 1.0 implementation
Microsoft's TLS 1.0 implementation is free of known security vulnerabilities. Due to the potential for future protocol downgrade attacks and other TLS 1.0 vulnerabilities not specific to Microsoft's implementation, it is recommended that dependencies on all security protocols older than TLS 1.2 be removed where possible (TLS 1.1/1.0/ SSLv3/SSLv2).
In planning for this migration to TLS 1.2+, developers and system administrators should be aware of the potential for protocol version hardcoding in applications developed by their employees and partners. Hardcoding here means that the TLS version is fixed to a version that is outdated and less secure than newer versions. TLS versions newer than the hardcoded version cannot be used without modifying the program in question. This class of problem cannot be addressed without source code changes and software update deployment. Protocol version hardcoding was commonplace in the past for testing and supportability purposes as many different browsers and operating systems had varying levels of TLS support.
Supported versions of TLS in Windows
Many operating systems have outdated TLS version defaults or support ceilings that need to be accounted for.
Figure 1: Security Protocol Support by OS Version
Windows Server 2019 GS edition is Microsoft SDL compliant, TLS 1.2 only with a restricted set of cipher suites.
Windows Server 2022 edition is Microsoft SDL compliant, TLS 1.2 and TLS 1.3 only with a restricted set of cipher suites.
TLS 1.1/1.2 can be enabled on Windows Server 2008 via this optional Windows Update package.
For more information on TLS 1.0/1.1 deprecation in IE/Edge, see Modernizing TLS connections in Microsoft Edge and Internet Explorer 11 , Site compatibility-impacting changes coming to Microsoft Edge and Disabling TLS/1.0 and TLS/1.1 in the new Edge Browser
A quick way to determine what TLS version will be requested by various clients when connecting to your online services is by referring to the Handshake Simulation at Qualys SSL Labs . This simulation covers client OS/browser combinations across manufacturers. See Appendix A at the end of this document for a detailed example showing the TLS protocol versions negotiated by various simulated client OS/browser combinations when connecting to www.microsoft.com .
If not already complete, it is highly recommended to conduct an inventory of operating systems used by your enterprise, customers and partners (the latter two via outreach/communication or at least HTTP User-Agent string collection). This inventory can be further supplemented by traffic analysis at your enterprise network edge. In such a situation, traffic analysis will yield the TLS versions successfully negotiated by customers/partners connecting to your services, but the traffic itself will remain encrypted.
Microsoft's Engineering Improvements to eliminate TLS 1.0 dependencies
Since the v1 release of this document, Microsoft has shipped a number of software updates and new features in support of TLS 1.0 deprecation. These include:
IIS custom logging to correlate client IP/user agent string, service URI, TLS protocol version and cipher suite.
- With this logging, admins can finally quantify their customers' exposure to weak TLS.
SecureScore - To help Office 365 tenant admins identify their own weak TLS usage, the SecureScore portal has been built to share this information as TLS 1.0 exited support in Office 365 in October 2018.
This portal provides Office 365 tenant admins with the valuable information they need to reach out to their own customers who may be unaware of their own TLS 1.0 dependencies.
Please visit https://securescore.microsoft.com/ for more information.
.Net Framework updates to eliminate app-level hardcoding and prevent framework-inherited TLS 1.0 dependencies.
Developer Guidance and software updates have been released to help customers identify and eliminate .Net dependencies on weak TLS: Transport Layer Security (TLS) best practices with the .NET Framework
- FYI: All apps targeting .NET 4.5 or below are likely going to have to be modified in order to support TLS 1.2.
TLS 1.2 has been backported to Windows Server 2008 SP2 and XP POSReady 2009 to help customers with legacy obligations.
More announcements will be made in early 2019 and communicated in subsequent updates of this document.
Finding and fixing TLS 1.0 dependencies in code
For products using the Windows OS-provided cryptography libraries and security protocols, the following steps should help identify any hardcoded TLS 1.0 usage in your applications:
Identify all instances of AcquireCredentialsHandle (). This helps reviewers get closer proximity to code blocks where TLS may be hardcoded.
Review any instances of the SecPkgContext_SupportedProtocols and SecPkgContext_ConnectionInfo structures for hardcoded TLS.
In native code, set any non-zero assignments of grbitEnabledProtocols to zero. This allows the operating system to use its default TLS version.
Disable FIPS Mode if it is enabled due to the potential for conflict with settings required for explicitly disabling TLS 1.0/1.1 in this document. See Appendix B for more information.
Update and recompile any applications using WinHTTP hosted on Server 2012 or older.
Managed apps – rebuild and retarget against the latest .NET Framework version
Applications must add code to support TLS 1.2 via WinHttpSetOption
To cover all the bases, scan source code and online service configuration files for the patterns below corresponding to enumerated type values commonly used in TLS hardcoding:
SecurityProtocolType
SSLv2, SSLv23, SSLv3, TLS1, TLS 10, TLS11
WINHTTP_FLAG_SECURE_PROTOCOL_
NSStreamSocketSecurityLevel
PROTOCOL_SSL or PROTOCOL_TLS
The recommended solution in all cases above is to remove the hardcoded protocol version selection and defer to the operating system default. If you are using DevSkim , click here to see rules covering the above checks which you can use with your own code.
Update Windows PowerShell scripts or related registry settings
Windows PowerShell uses .NET Framework 4.5, which does not include TLS 1.2 as an available protocol. To work around this, two solutions are available:
Modify the script in question to include the following:
Add a system-wide registry key (e.g. via group policy) to any machine that needs to make TLS 1.2 connections from a .NET app. This will cause .NET to use the "System Default" TLS versions which adds TLS 1.2 as an available protocol AND it will allow the scripts to use future TLS Versions when the OS supports them. (e.g. TLS 1.3)
reg add HKLM\SOFTWARE\Microsoft.NETFramework\v4.0.30319 /v SystemDefaultTlsVersions /t REG_DWORD /d 1 /f /reg:64
reg add HKLM\SOFTWARE\Microsoft.NETFramework\v4.0.30319 /v SystemDefaultTlsVersions /t REG_DWORD /d 1 /f /reg:32
Solutions (1) and (2) are mutually-exclusive, meaning they need not be implemented together.
Rebuild/retarget managed applications using the latest .Net Framework version
Applications using .NET framework versions prior to 4.7 may have limitations effectively capping support to TLS 1.0 regardless of the underlying OS defaults. Refer to the below diagram and Transport Layer Security (TLS) best practices with the .NET Framework for more information.

SystemDefaultTLSVersion takes precedence over app-level targeting of TLS versions. The recommended best practice is to always defer to the OS default TLS version. It is also the only crypto-agile solution that lets your apps take advantage of future TLS 1.3 support.
If you are targeting older versions of .NET Framework such as 4.5.2 or 3.5, then by default your application will use the older and not recommended protocols such as SSL 3.0 or TLS 1.0. It is strongly recommended that you upgrade to newer versions of .NET Framework such as .NET Framework 4.6 or set the appropriate registry keys for 'UseStrongCrypto'.
Testing with TLS 1.2+
Following the fixes recommended in the section above, products should be regression-tested for protocol negotiation errors and compatibility with other operating systems in your enterprise.
The most common issue in this regression testing will be a TLS negotiation failure due to a client connection attempt from an operating system or browser that does not support TLS 1.2.
- For example, a Vista client will fail to negotiate TLS with a server configured for TLS 1.2+ as Vista's maximum supported TLS version is 1.0. That client should be either upgraded or decommissioned in a TLS 1.2+ environment.
Products using certificate-based Mutual TLS authentication may require additional regression testing as the certificate-selection code associated with TLS 1.0 was less expressive than that for TLS 1.2.
- If a product negotiates MTLS with a certificate from a non-standard location (outside of the standard named certificate stores in Windows), then that code may need updating to ensure the certificate is acquired correctly.
Service interdependencies should be reviewed for trouble spots.
Any services which interoperate with 3 rd -party services should conduct additional interop testing with those 3 rd parties.
Any non-Windows applications or server operating systems in use require investigation / confirmation that they can support TLS 1.2. Scanning is the easiest way to determine this.
A simple blueprint for testing these changes in an online service consists of the following:
Conduct a scan of production environment systems to identify operating systems which do not support TLS 1.2.
Scan source code and online service configuration files for hardcoded TLS as described in " Finding and fixing TLS 1.0 dependencies in code "
Update/recompile applications as required:
Managed apps
Rebuild against the latest .NET Framework version.
Verify any usage of the SSLProtocols enumeration is set to SSLProtocols.None in order to use OS default settings.
WinHTTP apps – rebuild with WinHttpSetOption to support TLS 1.2
Start testing in a pre-production or staging environment with all security protocols older than TLS 1.2 disabled via registry .
Fix any remaining instances of TLS hardcoding as they are encountered in testing. Redeploy the software and perform a new regression test run.
Notifying partners of your TLS 1.0 deprecation plans
After TLS hardcoding is addressed and operating system/development framework updates are completed, should you opt to deprecate TLS 1.0 it will be necessary to coordinate with customers and partners:
Early partner/customer outreach is essential to a successful TLS 1.0 deprecation rollout. At a minimum this should consist of blog postings, whitepapers or other web content.
Partners each need to evaluate their own TLS 1.2 readiness through the operating system/code scanning/regression testing initiatives described in above sections.
Removing TLS 1.0 dependencies is a complicated issue to drive end to end. Microsoft and industry partners are taking action on this today to ensure our entire product stack is more secure by default, from our OS components and development frameworks up to the applications/services built on top of them. Following the recommendations made in this document will help your enterprise chart the right course and know what challenges to expect. It will also help your own customers become more prepared for the transition.
Appendix A: Handshake Simulation for various clients connecting to www.microsoft.com , courtesy SSLLabs.com

Appendix B: Deprecating TLS 1.0/1.1 while retaining FIPS Mode
Follow the steps below if your network requires FIPS Mode but you also want to deprecate TLS 1.0/1.1:
Configure TLS versions via the registry , by setting "Enabled" to zero for the unwanted TLS versions.
Disable Curve 25519 (Server 2016 only) via Group Policy.
Disable any cipher suites using algorithms that aren't allowed by the relevant FIPS publication. For Server 2016 (assuming the default settings are in effect) this is means disabling RC4, PSK and NULL ciphers.
Contributors/Thanks to
Mark Cartwright Bryan Sullivan Patrick Jungles Michael Scovetta Tony Rice David LeBlanc Mortimer Cook Daniel Sommerfeld Andrei Popov Michiko Short Justin Burke Gov Maharaj Brad Turner Sean Stevenson
Was this page helpful?
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback .
Submit and view feedback for
Additional resources

IMAGES
VIDEO
COMMENTS
TLS security. iOS, iPadOS, and macOS support Transport Layer Security (TLS 1.0, TLS 1.1, TLS 1.2, TLS 1.3) and Datagram Transport Layer Security (DTLS). The TLS protocol supports both AES128 and AES256, and prefers cipher suites with forward secrecy. Internet apps such as Safari, Calendar, and Mail automatically use this protocol to enable an ...
Safari: To enable TLS 1.1 and 1.2 in Safari, perform the following steps: 1. There are no options for enabling SSL or TLS protocols. If you are using Safari version 7 or
Older web browsers use out-of-date protocols that do not support modern encryption and contain security vulnerabilities that can be exploited by attackers. Effective July 1, 2021, only web browsers that support versions 1.2 or 1.3 of the Transport Layer Security (TLS) protocol will be permitted to access University web services.
Scroll down to Security category, manually check the option box for Use TLS 1.1 and Use TLS 1.2 Click OK; Close your browser and restart Google Chrome; Mozilla Firefox. Open Firefox; In the address bar, type about:config and press Enter; In the Search field, enter tls. Find and double-click the entry for security.tls.version.max
Scroll down to Security category, manually check the option box for Use TLS 1.1 and Use TLS 1.2; Click OK; Close your browser and restart Google Chrome; Mozilla Firefox. Open Firefox; In the address bar, type about:config and press Enter; In the Search field, enter tls. Find and double-click the entry for security.tls.version.min
One way of checking which protocol is being used by a certain URL is to run in OS X terminal the following utility: nscurl --ats-diagnostics <YOUR URL> --verbose. - miranido. Jun 18, 2017 at 13:21. Thanks @miranido, this is the right way to detect the flaw in the implementation. - Gaurav Shishodia.
Open Firefox. In the address bar, type about:config and press Enter. In the Search field, enter tls. Find and double-click the entry for security.tls.version.max. Set the integer value to 3 or higher to force protocol of TLS 1.2 or higher. For security.tls.version.min set the integer value to 3 to force protocol of TLS 1.2. Click OK.
SSL, or Secure Sockets Layer, is the predecessor to TLS. It was a cryptographic protocol developed by Netscape in 1994, but since it had serious flaws, it was never released to the public. SSL 2.0 was released publicly one year later, in 1995, but it, too, was found to have serious flaws. Finally, SSL 3.0 was rebuilt from the ground up and ...
Reddit. Apple this week continued work to deprecate Transport Layer Security 1.0 and 1.1 from its various operating systems, replacing the long-in-the-tooth security protocols with more modern ...
Safari 6.0.4/OS X10.8.4 and earlier versions; Resolution. Upgrade to a later version of the browser. Azure App Service doesn't use the latest version of TLS and .NET Framework Symptom. Authentication issues when you use Azure App Service. Resolution. Set the minimum TLS version for your App Service instance to TLS 1.2.
TLS, or Transport Layer Security, is a security protocol used to protect web traffic. Ahead of the planned deprecation, Apple recommends apps adopt TLS 1.2, which offers "security fit for the ...
From June 1, 2021, Write-n-Cite will support TLS 1.2 only and will not support earlier versions. Refer to the flowchart or table below for details on checking if your system supports TLS 1.2. Make sure you meet requirements A, B and C.
Version history for TLS/SSL support in web browsers tracks the implementation of Transport Layer Security protocol versions in major web browsers . ^ Note actual security depends on other factors such as negotiated cipher, encryption strength, etc. (see § Cipher table). ^ Whether a user or administrator can choose the protocols to be used or not.
Manually enabling TLS 1.2 on web browsers Mozilla Firefox 1. Open Firefox 2. In the address bar, type about:config and press Enter 3. In the Search field, enter tls. Find and double-click the entry for security.tls.version.max 4. Set the integer value to 3 to force protocol of TLS 1.2 5. Click OK 6. Close your browser and restart Mozilla Firefox
Everything is working fine, however I want to add code to ensure only TLS 1.2 connections are allowed. I cannot find any way to configure this in the https.agent options, or elsewhere. Is it possible to configure this, or do I have to make a connection and then query the protocol version, with something like: res.socket.getProtocol() === 'TLSv1.2'
Transport Layer Security (TLS), like Secure Sockets Layer (SSL), is an encryption protocol intended to keep data secure when being transferred over a network. These articles describe steps required to ensure that Configuration Manager secure communication uses the TLS 1.2 protocol.
Mozilla Firefox. Open Firefox. In the address bar, type about:config and press Enter. In the Search field, enter tls. Find and double-click the entry for security.tls.version.min. Set the integer value to 3 to force protocol of TLS 1.2 to be the default. Click OK. Close your browser and restart Mozilla Firefox.
Just as a reminder, TLS protocol negotiation works as follows: In the Client Hello message, the client sends the server the maximum TLS version it supports and the list of cypher suites it supports.. The server looks at those and picks its preferred TLS version and cypher suite, sending that back to the client in the Server Hello message. Alternatively, if there's no choice that's ...
The TLS (stands for Transport Layer Security) protocol is an upgrade to the previously used Secure Sockets Layer (SSL) protocol. Netscape invented SSL because it realized that at least some uses ...
Brad Turner. Sean Stevenson. This document presents guidance on rapidly identifying and removing Transport Layer Security (TLS) protocol version 1.0 dependencies in software built on top of Microsoft operating systems. It is intended to be used as a starting point for building a migration plan to a TLS 1.2+ network environment.
Yup, you got that right! Earlier macOS used to have Internet Explorer, but Safari changed that. A Windows compatible version of the Safari browser was also offered from 2007 to 2010. The Safari browser is considered to be the best way to experience the Internet through an Apple devices.
In the TLS handshake the server will choose the best protocol supported by the client. Given that the connection only results in TLS 1.0 if your client is connecting to a server which support TLS 1.0...TLS 1.2 it looks like your (unknown) client only supports TLS 1.0. In this case it is no surprise that it will fail if the server has only TLS 1 ...
Craig. 1. If all protocols are allowed, you have to check whether the GAC includes al least .NET 4.5 (.NET 4.6.1 would be better if the platform supports it). Then (if you can't recompile) force the ServicePointManager to include TLS 1.2 among the protocols used in the SSL handshake: ServicePointManager.SecurityProtocol ...